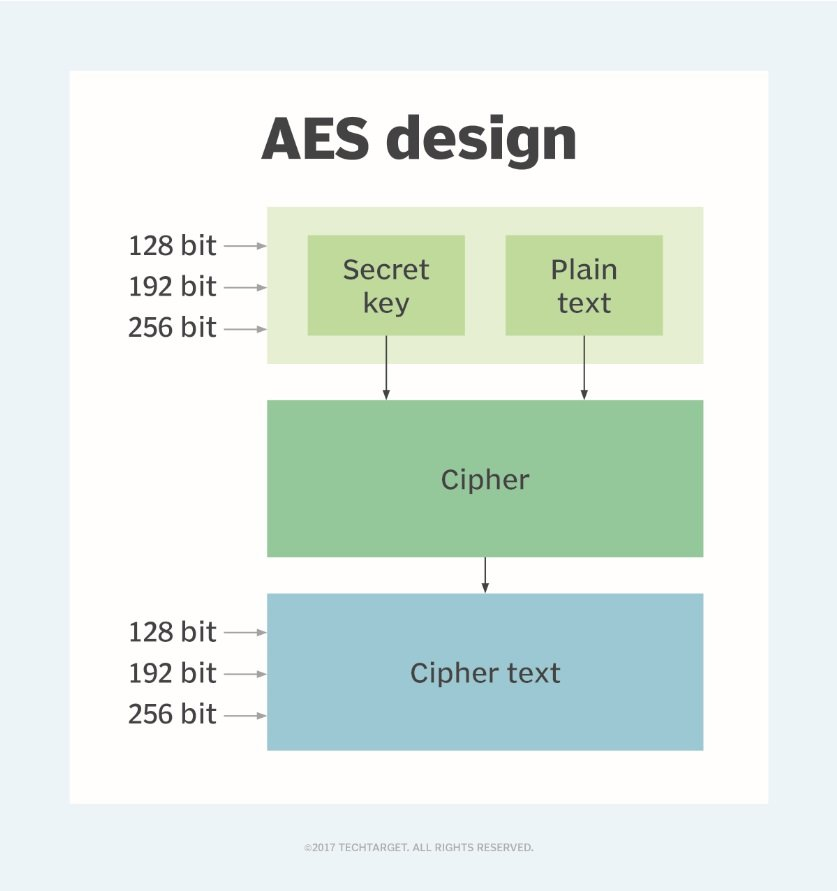
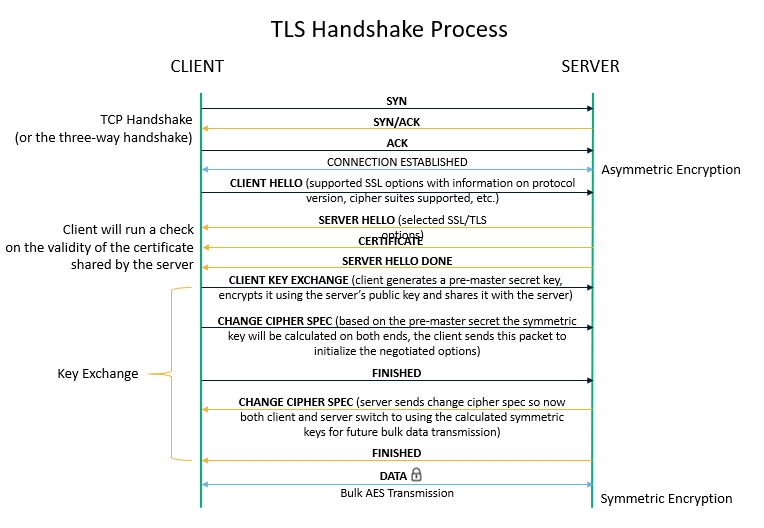
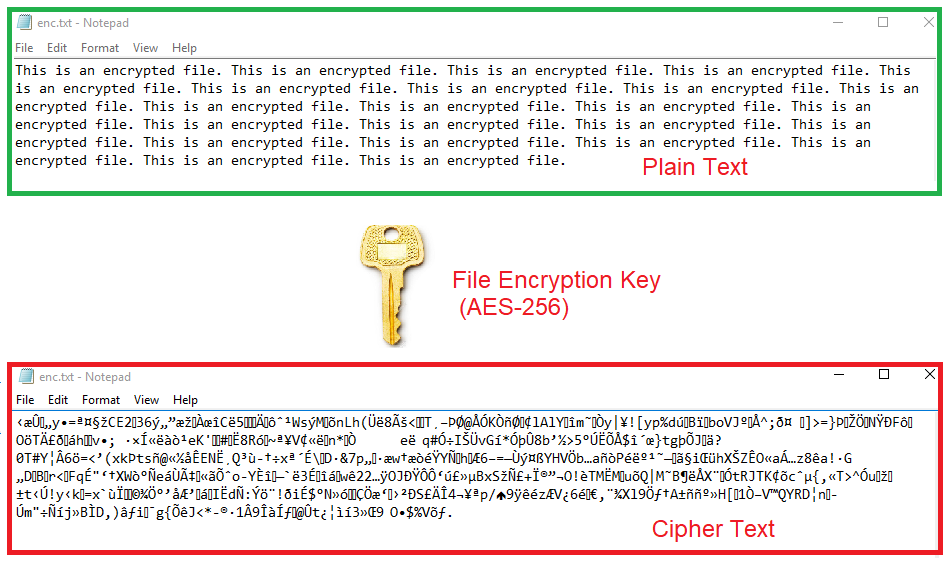
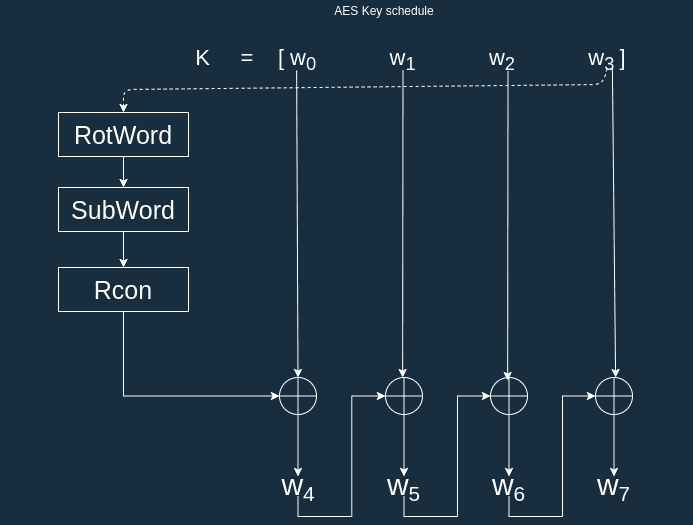
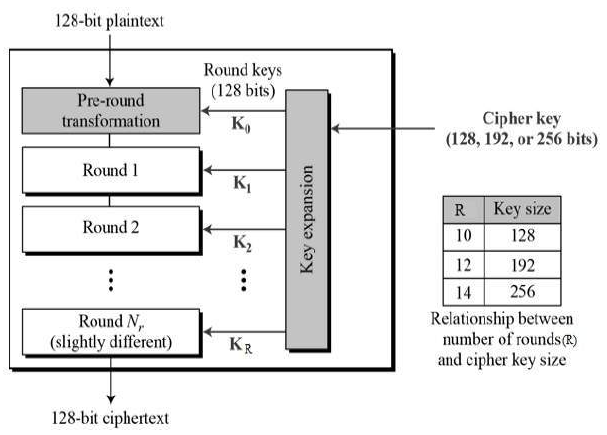
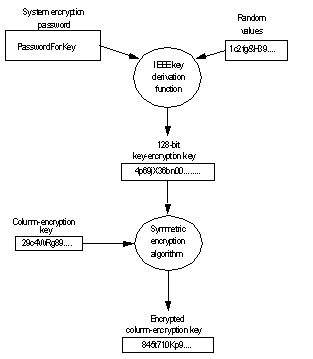
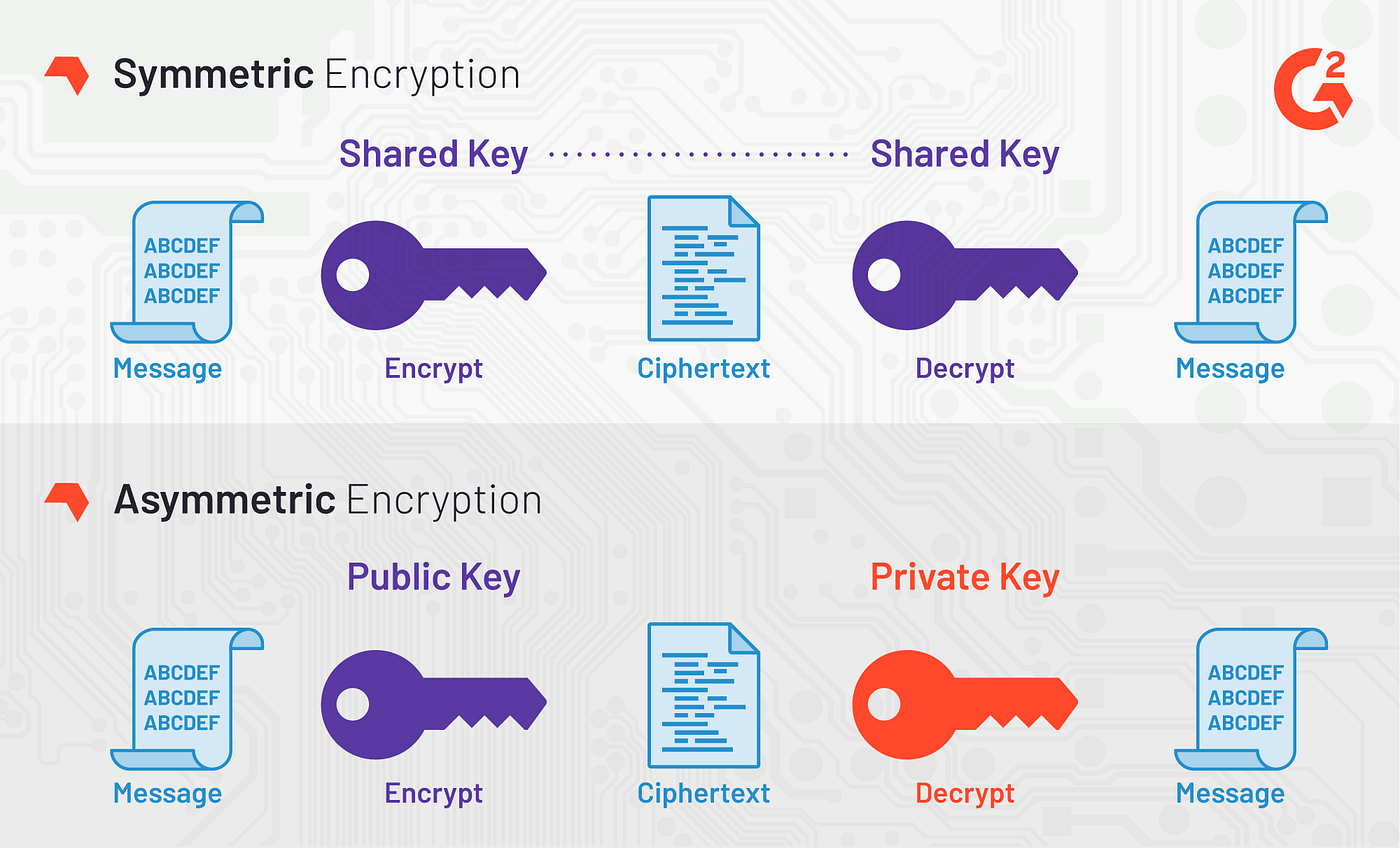
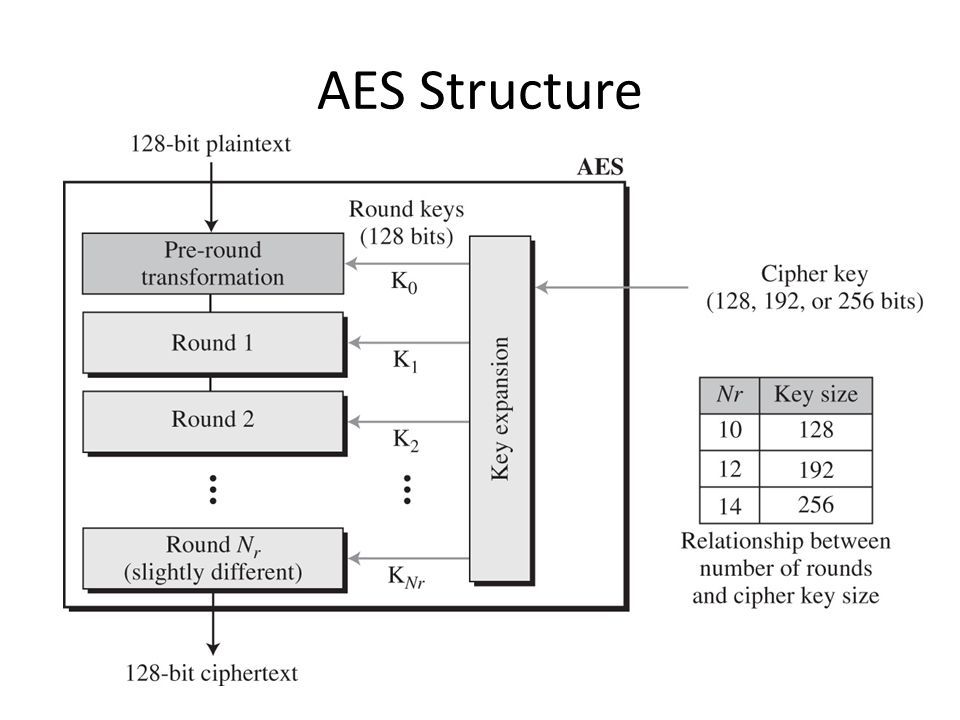
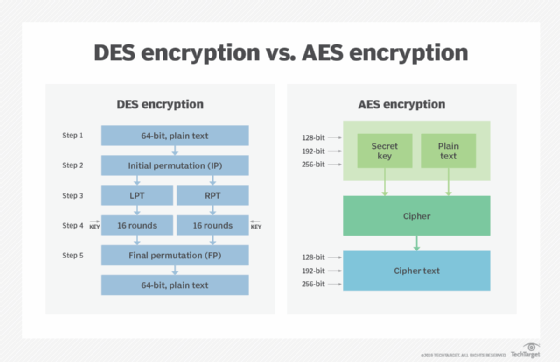
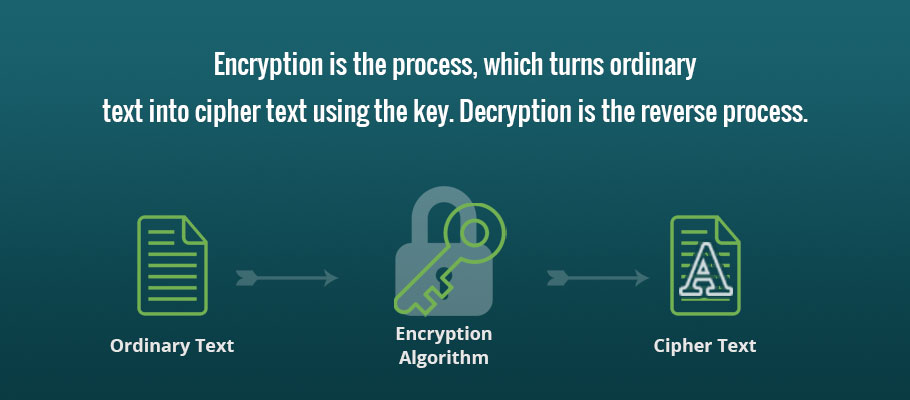
GitHub - rexdivakar/InstaEncrypt: This is an Open Source AES Standard encryption tool. It uses asymmetric-key algorithm, for both encrypting and decryption the data.

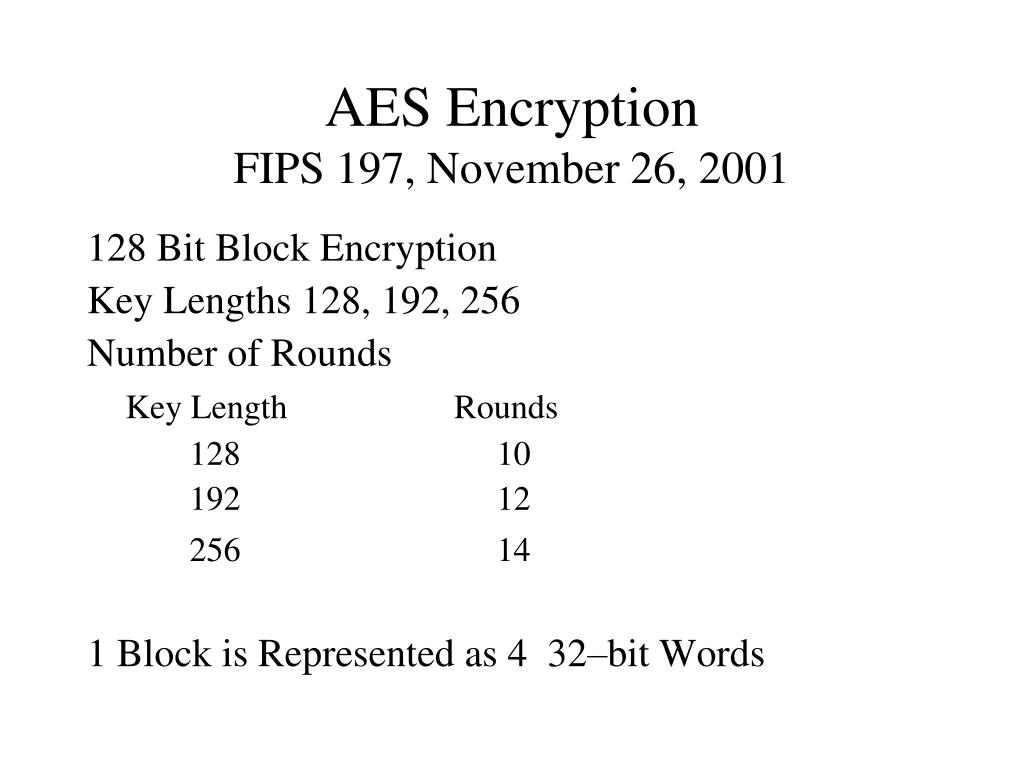
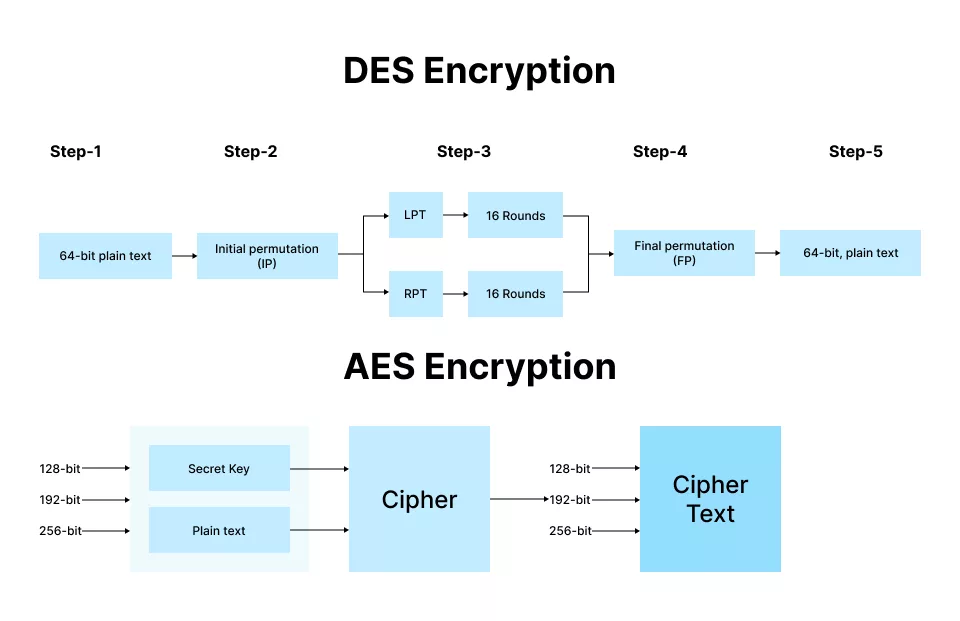
What's the deal with encryption strength —is 128 bit encryption enough or do you need more? | by Lance Gutteridge | Medium