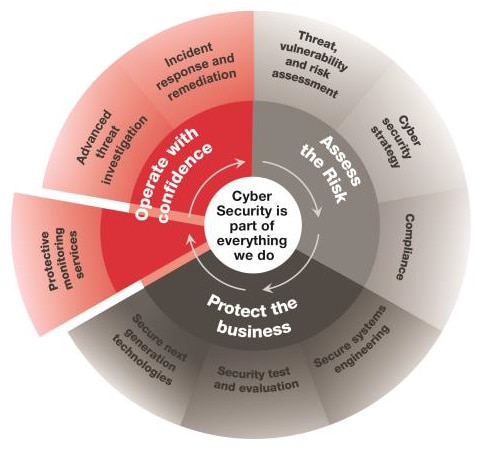
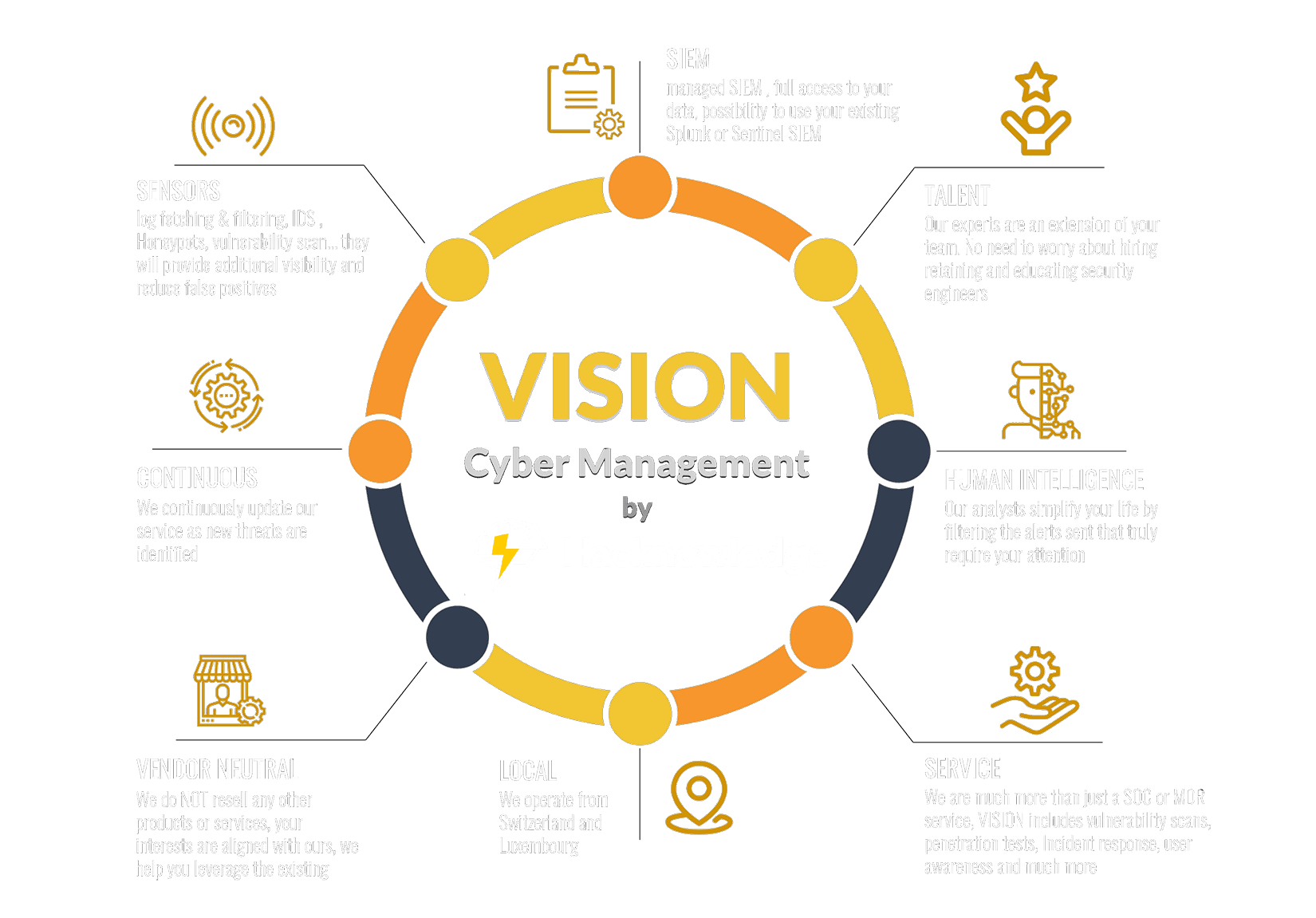
Vijilan Security's Cybersecurity Monitoring: Empowering Businesses with Proactive Threat Detection and Rapid Incident Response
HUD security monitoring system technology, digital interface screen, vector UI. HUD cyber security monitor, target location detection or positioning and spy surveillance in global cybersecurity system Stock-Vektorgrafik | Adobe Stock
![PDF] An integrated cyber security monitoring system using correlation-based techniques | Semantic Scholar PDF] An integrated cyber security monitoring system using correlation-based techniques | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/58968c70bbb41db3574ccb48cf74d6a55f4482a3/2-Figure1-1.png)