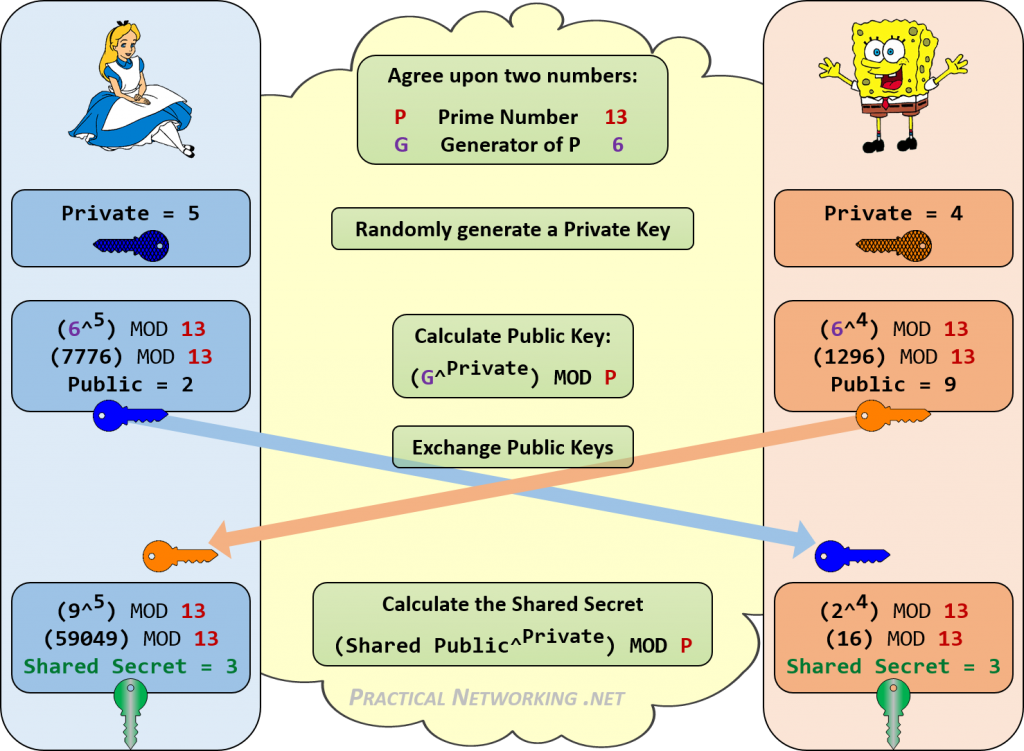
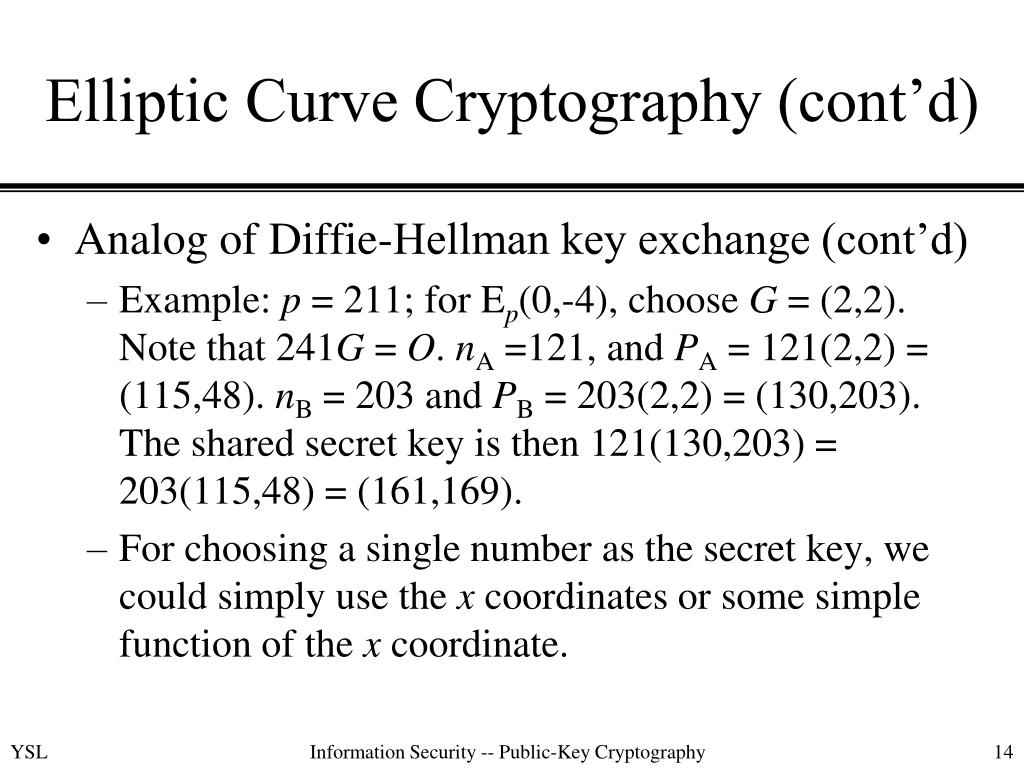
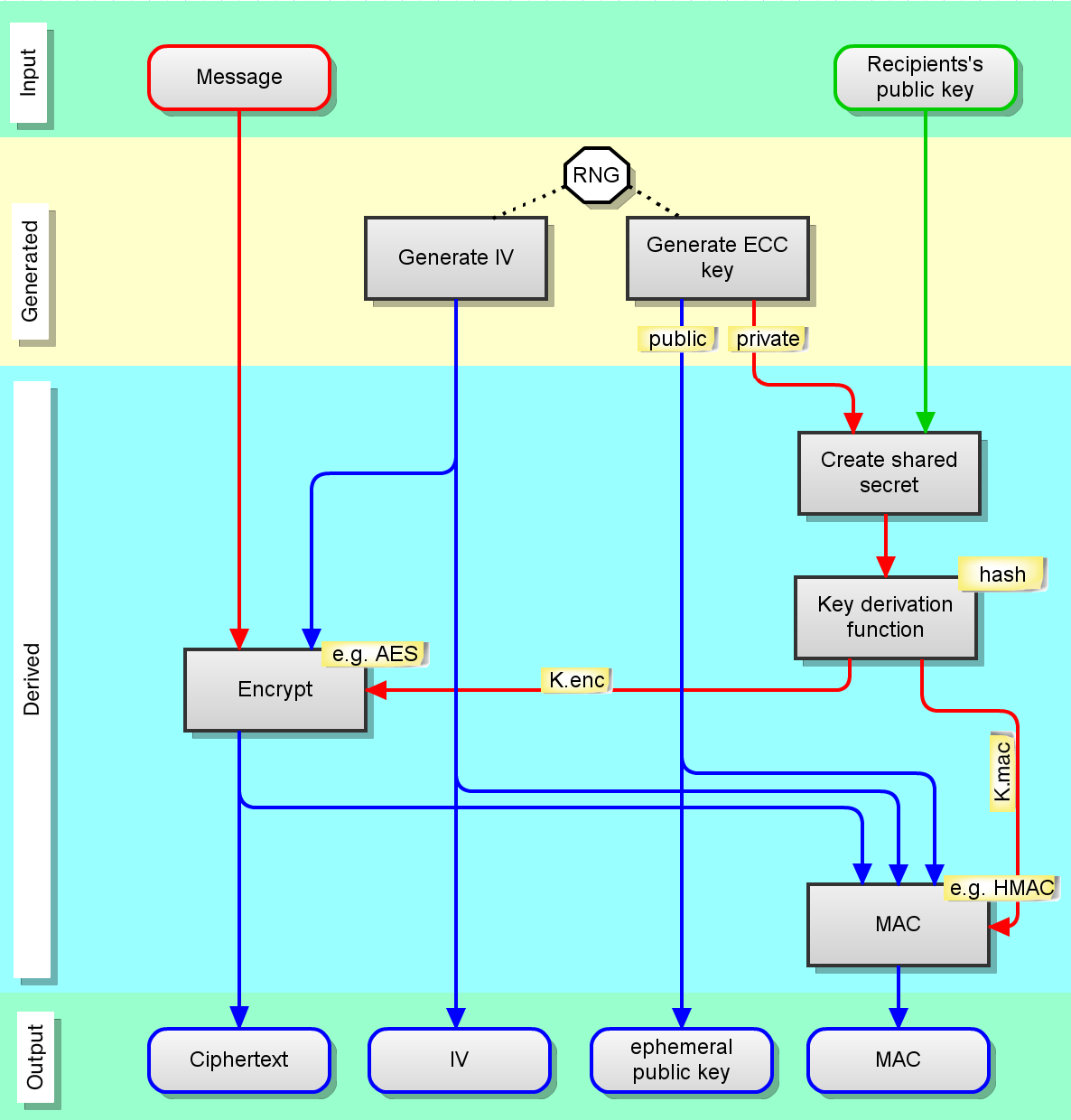
Figure 4 from Enhanced Elliptic Curve Diffie-Hellman Key Exchange Algorithm for Ornamental Security based on Signature and Authentication Algorithm | Semantic Scholar
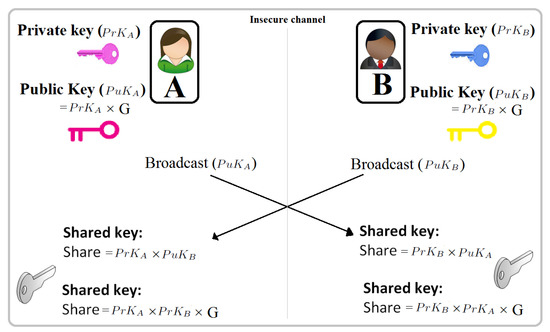
Symmetry | Free Full-Text | Implication of Lightweight and Robust Hash Function to Support Key Exchange in Health Sensor Networks

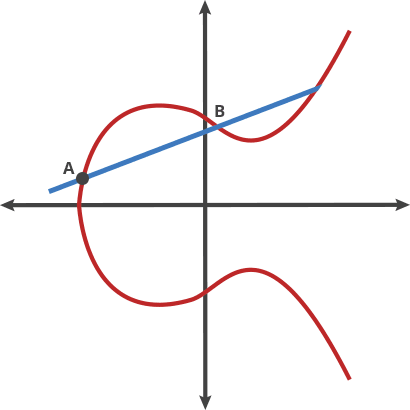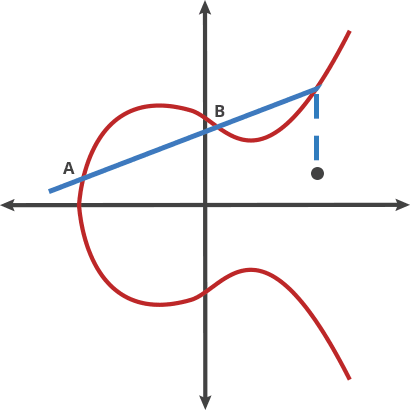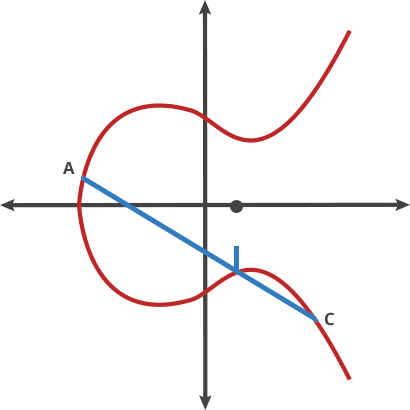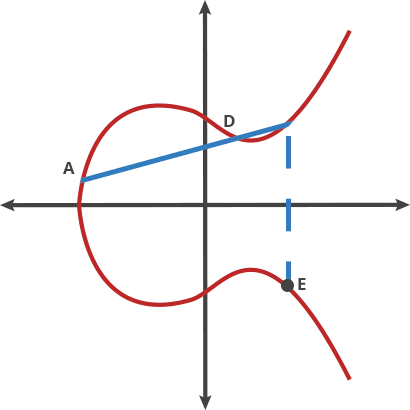


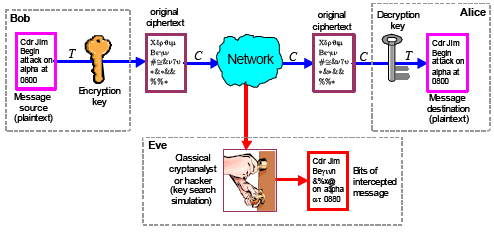

![PDF] The Elliptic Curve Diffie-Hellman (ECDH) | Semantic Scholar PDF] The Elliptic Curve Diffie-Hellman (ECDH) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/de032e79b6116aeb3efc26de258903d6fdc24a08/1-Figure1-1.png)